As a detection engineer or analyst, you’ll probably enable dozens of detections that come out of the box with whatever SIEM you’re using, be it Splunk, Sentinel, Elastic or anything else. While reviewing some file creation events, I noticed something (neat?): Sentinel/Microsoft Edge does this thing where it’ll render emojis really nicely, even in the log-view:
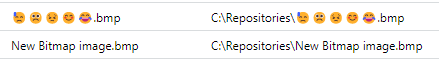
This made me think, as an attacker, could I bypass a whole bunch of pre-canned SIEM detections using this? And as a defender, can we somehow bake-in support for querying Unicode?
Not really. I tried querying in Sentinel for the Unicode string for that ‘crying with laughter’ emoji and no hits. Tried the hex, no hits. It only worked if I used the actual emoji itself.
It’s only a small thing — I doubt 99% of real world attackers would even care — and I doubt you could get past a sophisticated EDR with such a novel ‘obfuscation’ technique — but it’s food for thought next time you’re working on a red team assessment. It’s doubly effective at confusing the hell out of whatever analyst is reviewing the logs. It also further proves why we need good behavioural detections, rather than hard-coded paths and binary names.
If you know of any research around this topic and using emojis to obfuscate badness, please DM me!