In late November, the Defender log schema in Sentinel were updated to include a new entry in the 'ActionType' category - Network signature inspected.
DeviceNetworkEvents
| where ActionType == 'NetworkSignatureInspected'
By filtering these events further, we can derive the specific signature name of the protocol that was inspected by Defender.
DeviceNetworkEvents
| where ActionType == 'NetworkSignatureInspected'
| extend SignatureName_ = tostring(AdditionalFields.SignatureName)
| summarize count() by SignatureName_
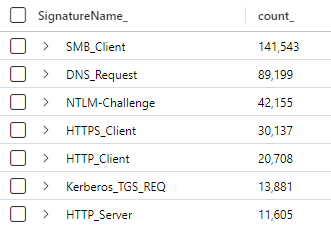
I haven't seen much publicised about this change, and I suspect this enhanced logging is resultant of the recent integration with Zeek. These events are a solid lead when conducting threat hunts, but of course be wary of the pitfalls of Defender logging and the heavy sampling Microsoft do (these are no replacement for Firewall events!).